GRAV - correctly redirect HTTP to HTTPS
The new normal of web development pretty much requires us to use HTTPS. We use the GRAV CMS heavily, and you might wonder what the correct way to direct to HTTPS.
What is the purpose of HTTPS?
First, let's explain what HTTPS is and why are search engines like google requiring this protocol.
Hypertext transfer protocol secure (HTTPS) is the secure version of HTTP. HTTP is the primary protocol used to send data between your device's web browser and the website you are looking up; this is why websites start with http://www.etc-ect.com.
When using the secure version of HTTP, you will see in your address bar a "lock" or the word "secure" normally highlighted in green. HTTPS is encrypted, increasing the end-user (visitors) security during the transfer of data.
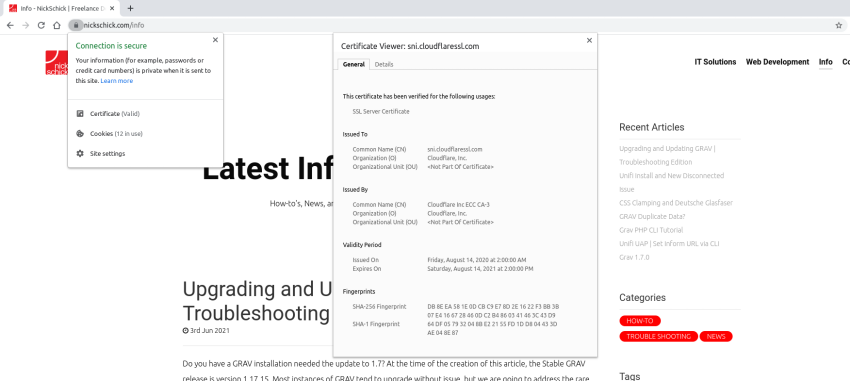
Consider why this would be important, protecting your users when sending login data or banking or payment data.
How does HTTPS work?
HTTPS uses an encryption protocol to encrypt the data transmitted. Transport Layer Security (TLS) is the security protocol used, which communicates with an asymmetric public key infrastructure. The protocol had been known as Secure Sockets Layer (SSL) and is still used to describe the product used to secure a website, which can be confusing. TLS uses two different keys to encrypt communications between two parties, e.g. the browser and a website.
How do the keys work
There are two keys, a private key, and a public key. The private key is kept on the webserver and is used to decrypt information. The public key is publically available and is used to encrypt the data sent over the net, only to be decrypted by the private key. It is important to note that all data that is encrypted by the public key; can only be decrypted by the private key.
Below is an example of how this could look:
<h1>This is a title</h1>
<p>And here are details</p>the result wouild be
441d4c69d2907623f01767ee113972e9e19ac9f5e0454bf6239327c25292716b86f39c4456aec7ff0faeab728ae9591fb0b94eb8294b13b4a085b78a525fc8d9But Users need to access HTTPS
Without adjusting your web application, your users will typically access the HTTP version of your website. Meaning to access the HTTPS version of your web application, the user must type in "https://" before the address they are view. There are some ways to adjust this permanently, one of them being HTTP Strict Transport Security or HSTS.
HTTP Strict Transport Security
HTTP Strict Transport Security (HSTS) is a policy mechanism that helps to protect websites against man-in-the-middle attacks such as protocol downgrade attacks[1] and cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should automatically interact with it using only HTTPS connections, which provide Transport Layer Security (TLS/SSL), unlike the insecure HTTP used alone. HSTS is an IETF standards track protocol and is specified in RFC 6797.
The HSTS Policy is communicated by the server to the user agent via an HTTPS response header field named "Strict-Transport-Security". HSTS Policy specifies a period of time during which the user agent should only access the server in a secure fashion. Websites using HSTS often do not accept clear text HTTP, either by rejecting connections over HTTP or systematically redirecting users to HTTPS (though this is not required by the specification). The consequence of this is that a user-agent not capable of doing TLS will not be able to connect to the site.
The protection only applies after a user has visited the site at least once, relying on the principle of Trust on first use. The way this protection works is that a user entering or selecting a URL to the site that specifies HTTP, will automatically upgrade to HTTPS, without making an HTTP request, which prevents the HTTP man-in-the-middle attack from occurring.
Source: wikipedia
HSTS is trouble-free; to use HSTS you must adjust your response headers; it has a time limit, and not all browsers support this technology. If you're hosted with a provider like FullSail Systems or use a DNS proxy service like Cloudflare, HSTS is built into your response headers already.
If you are not using these services, there are other ways to accomplish them. There are many ways, but we will only cover two methods, the GRAV system or .htaccess, which works in 99.9% of scenarios.
How do we implement HTTPS in GRAV?
Grav allows you to force HTTPS redirections using the core configuration file or admin plugin.
Note:
Grav recommends using the .htaccess method for the best web performance.
Using the built-in tools from GRAV
Like all tasks in GRAV, there are few ways to accomplish a task like HTTPS redirections. To redirect to the secure version of your application, we suggest one of these two simple methods: CLI (FTP/SSH) or Admin Plugin.
Note:
To use HTTPS, you as the website owner must provide an SSL Cert. SSL's are a completely different topic but must be present to activate successfully.
CLI (FTP/SSH)
Using your favorite FTP software, file transfer system, or terminal to perform these steps:
- Log into your server via SSH, Use your server's file manager or access the server via FTP
- Navigate to the
{GRAV_ROOT_DIRECTORY}/user/config folder - Locate and Open the file
system.yaml - Locate the entry force_ssl and change from false to true
- Save your changes
Admin Plugin (Admin GUI / Backend)
You can also change this setting in the Admin Plugin:
Note:
This method will only work when you have the GRAV Admin Plugin installed and configured.
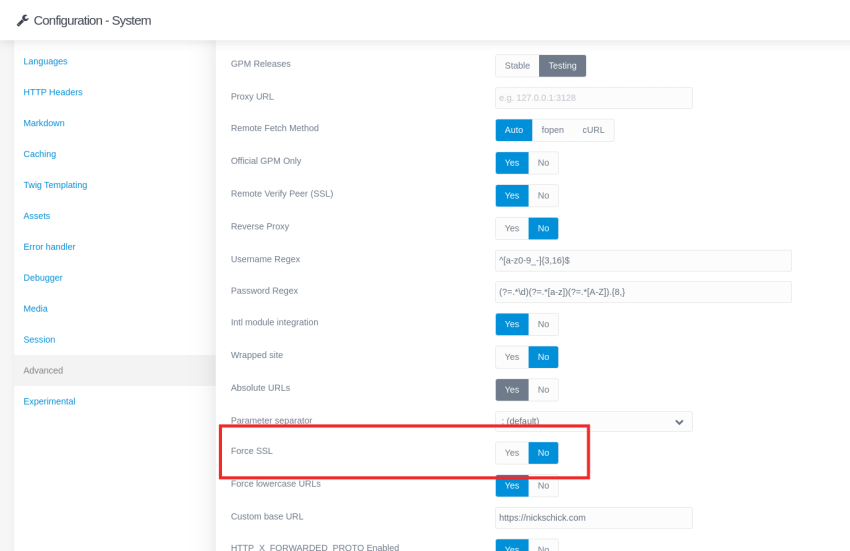
- Log into the Admin Plugin of GRAV
- Select Configuration
- Navigate to the Systems tab and select Advanced on the left
- Towards the bottom, find Force SSL and select Yes
- Click Save at the top
.htaccess for a performance boost
As recommended by GRAV and what we typically implement is a redirection via .htaccess. We need to change one file that instructs your webserver to redirect port 80 to port 443 (the port designated for HTTPS).
Note:
The .htaccess file is native to the Apache webserver. Meaning, if you are using Nginx, an .htaccess file will not be read or implemented. We will not cover how to modify the man Nginx configuration directive to accomplish the same goal.
- Log into to your server via SSH, Use your servers file manager or access the server via FTP.
- Navigate to your root directory
- Locate and Open the file
.htaccess(if it does not exisit, you must create it) - You are going to need to place this information at the top of this file.
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
- Save your changes and you are done
Wrapping Up
There are many ways to accomplish this goal, but make it as easy for your visitors as possible. Meaning in one way or another, you must redirect to a secure version of your site automatically.
We hope you found this information helpful, and if you have any questions or need help with your web application or technical infrastructure, we are

